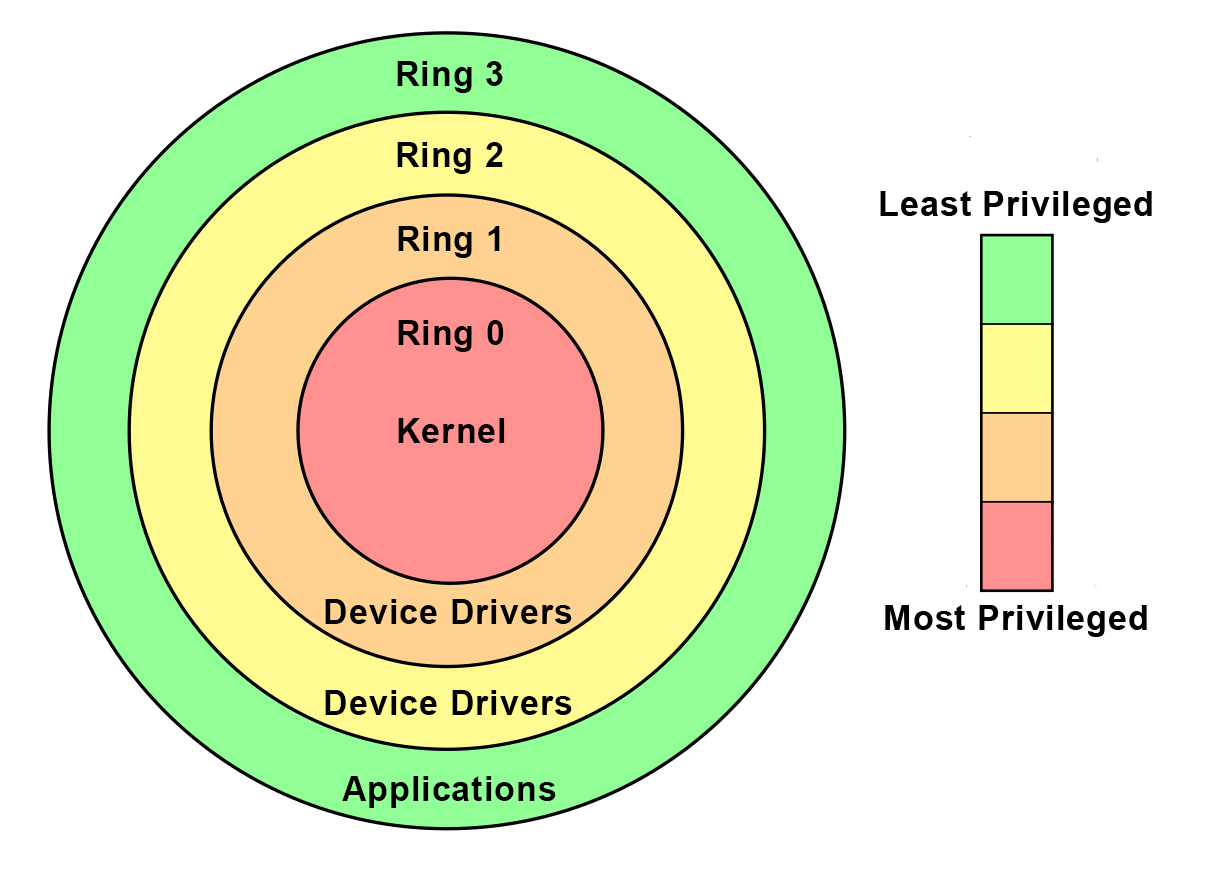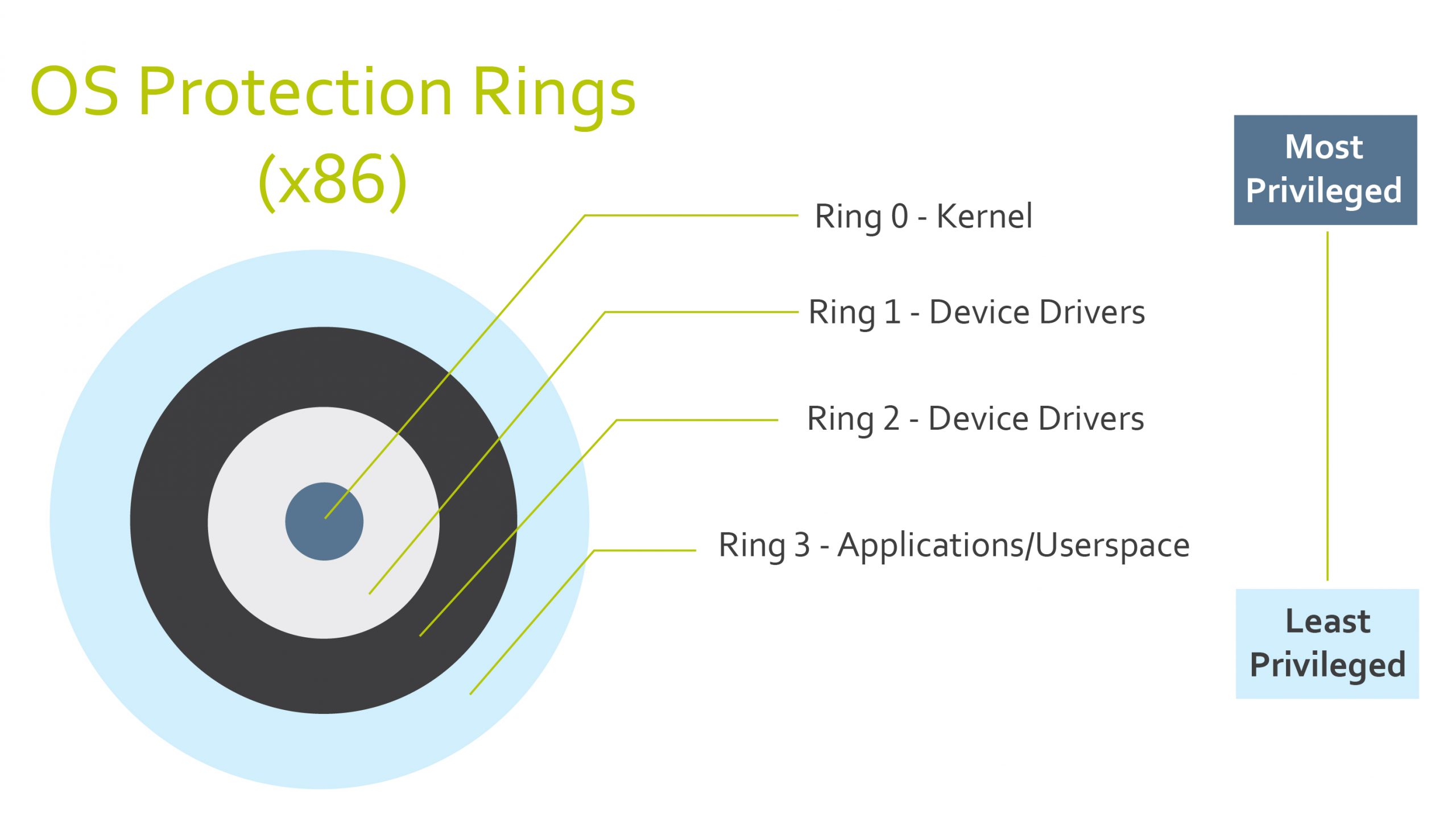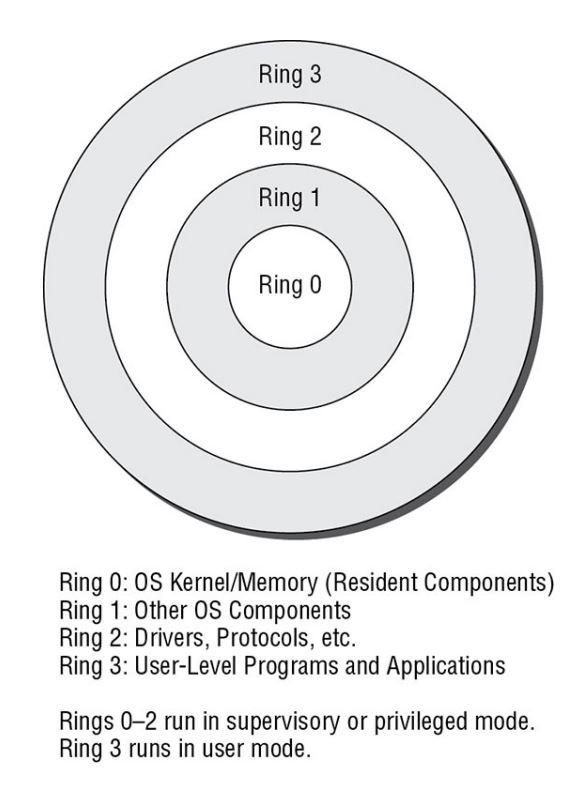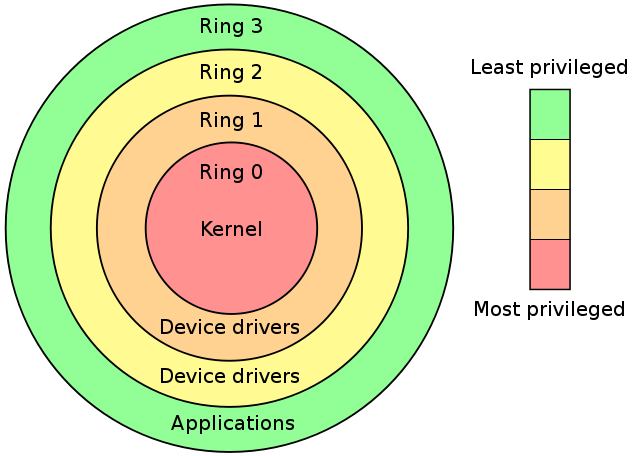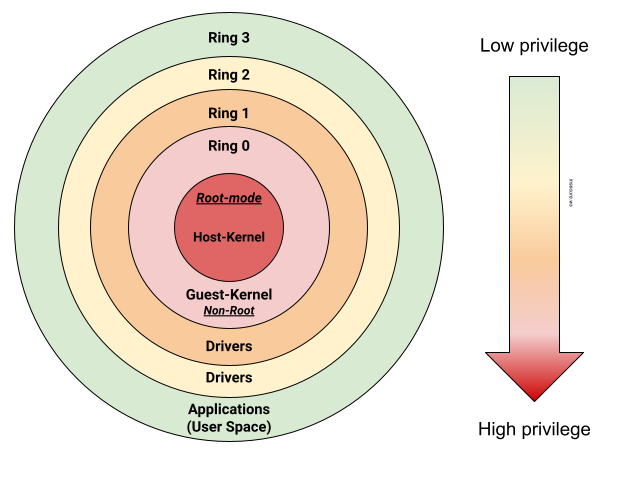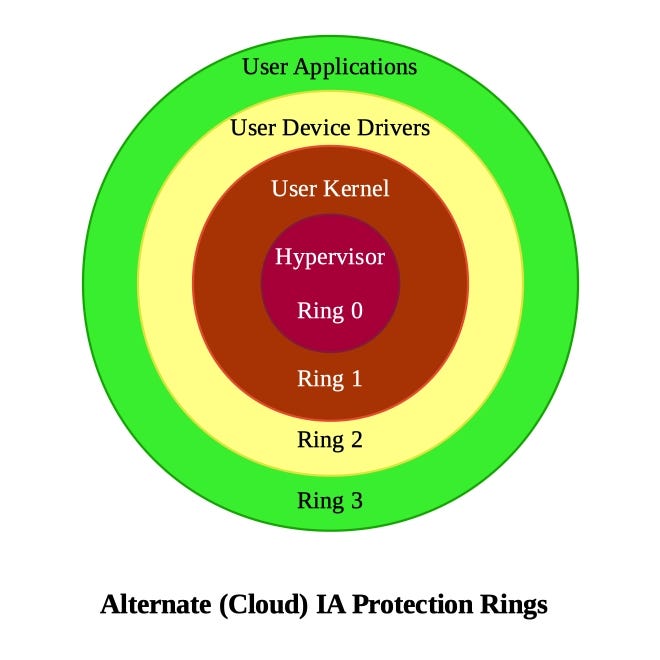
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium

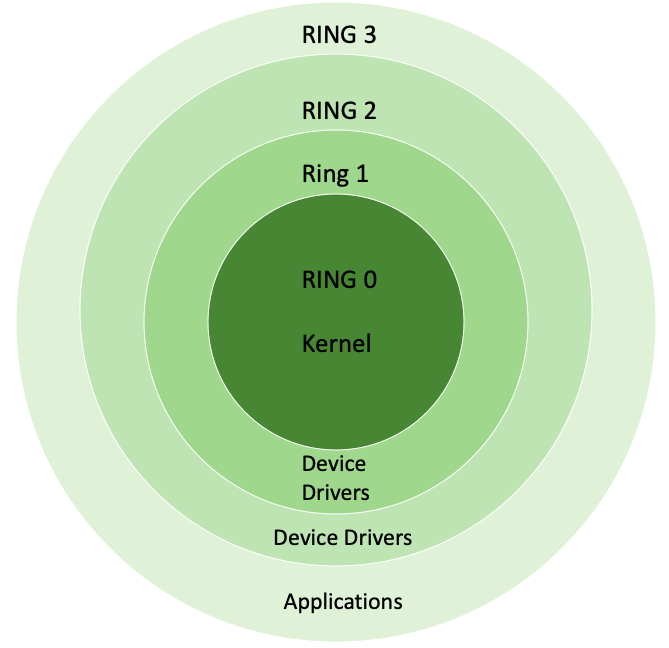
What is kernel rings in a system ? | kernel protection ring | cloudpradeep | by cloud pradeep | Medium